MetaMask phishing has emerged as a significant threat in the cryptocurrency landscape, with hundreds of wallets recently drained through deceptive tactics. Cybercriminals have crafted convincing emails that impersonate legitimate MetaMask communications, tricking users into revealing sensitive information. This alarming trend has raised concerns about MetaMask security and the safety of crypto wallets overall, as victims suffer losses averaging under $2,000 per incident. Understanding the nuances of phishing scams is crucial for effective wallet protection, especially amid the increasing sophistication of these attacks. To better safeguard against such threats, users must not only be vigilant against phishing attempts but also adopt robust blockchain security practices to protect their digital assets.
The phenomenon of wallet compromise via misleading emails designed to imitate MetaMask communications reflects a growing trend in online scams targeting cryptocurrency users. Such attacks, often described as phishing schemes, have resulted in significant asset depletion for unsuspecting victims, raising urgent questions about crypto wallet safety. In the face of such risks, it’s vital for users to familiarize themselves with effective wallet protection tips and to stay updated on best practices for maintaining cybersecurity. As attackers continue to exploit vulnerabilities, enhancing MetaMask security through awareness and proactive measures becomes essential for safeguarding individual assets. By acknowledging these threats and adopting a multi-layered approach to security, crypto enthusiasts can reduce their chances of falling victim to future scams.
Understanding MetaMask Phishing Attacks
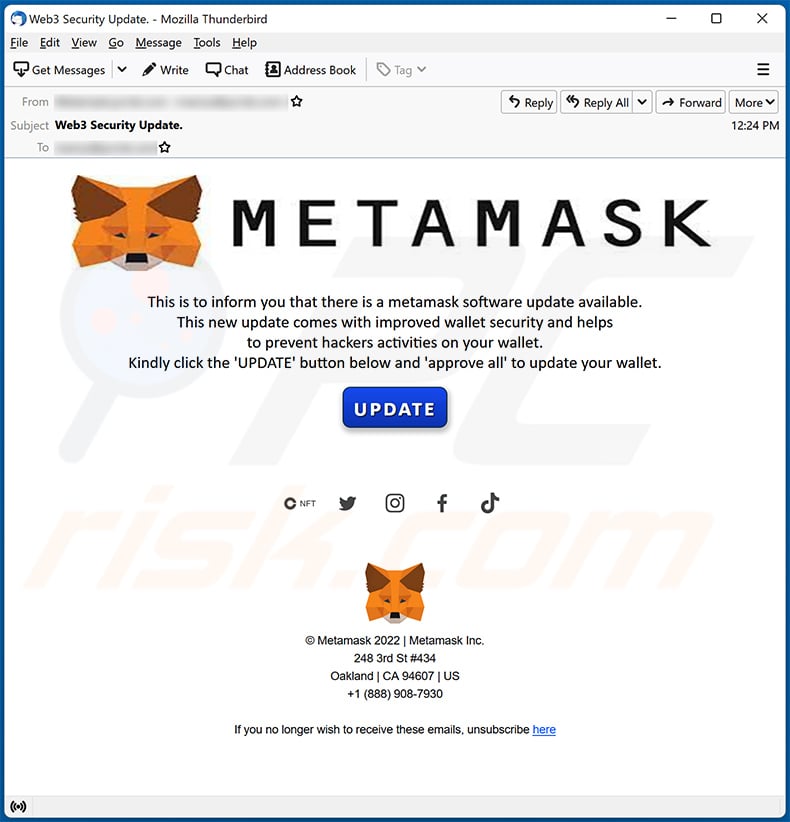
MetaMask phishing attacks are a growing concern in the cryptocurrency landscape, especially as they become increasingly sophisticated. Cybercriminals often leverage well-crafted emails that appear legitimate, such as those purporting to be from MetaMask, to trick users into revealing sensitive information or approving malicious transactions. The recent incident involving hundreds of wallet drainages highlights this trend, as individuals received emails disguised as urgent MetaMask updates. These attacks exploit seasonal occasions, creating a sense of urgency that catches users off guard, thereby facilitating their schemes more effectively.
To protect against such phishing scams, users should remain vigilant and aware of potential red flags. Common indicators include mismatched sender addresses that do not originate from verified MetaMask domains, unsolicited demands for action, and any requests for personal credentials like Secret Recovery Phrases. By understanding these warning signs, individuals can better shield their assets against phishing risks that target crypto wallet security.
Wallet Protection Tips to Safeguard Your Assets
The security of a cryptocurrency wallet, such as MetaMask, hinges on appropriate protective measures that users can implement to stave off potential threats. A primary strategy involves revoking contract permissions that were granted to untrusted applications or during previous transactions. MetaMask’s built-in features, alongside tools like Revoke.cash, empower users to scrutinize and manage their token approvals, curbing unauthorized access to their assets. This practice of proactive wallet management can significantly minimize the risks associated with unauthorized transactions.
Another essential strategy for wallet protection is the segregation of holdings across multiple wallets. By distributing assets among various digital wallets, users reduce the risk of catastrophic losses should one wallet become compromised. Employing a tiered approach—where small amounts are held in software wallets for regular transactions, while significant investments are secured in hardware wallets—adds an additional layer of security. This diversified approach enables users to engage with the crypto space actively, whilst still maintaining strict defenses against potential phishing attacks.
The Importance of Blockchain Security Awareness
Blockchain security awareness is crucial for all cryptocurrency users, especially in the face of evolving threat landscapes characterized by phishing scams and wallet compromises. The recent surge in compromised wallets illustrates a significant trend where attackers target individuals with minimal security habits. As custodians of their digital assets, users must prioritize education on best practices for isolating risks associated with wallet usage and transaction approvals.
Additionally, understanding the composition of blockchain technology itself—the decentralized nature of transactions and pseudonymous identities—can help users appreciate the importance of adherence to security protocols. Knowledge of how attackers exploit vulnerabilities enhances user resilience against phishing attempts, leading to more robust security practices that defend against crypto wallet threats. Through diligent education, users can better navigate their cryptocurrency journeys while minimizing potential exposure to risks.
Recognizing the Signs of Phishing Scams
Recognizing the signs of phishing scams is essential for safeguarding your crypto wallet and assets. Phishing attempts may initially appear benign, employing familiar branding or relevant seasonal themes to appear reliable. In the case of the MetaMask phishing email, the fraudulent sender used a name closely associated with decentralized finance to deceive users. Signs such as poor spelling, mismatched URLs, or unsolicited requests for private information are often telltale indicators of phishing attempts.
Moreover, recognizing that genuine wallet providers, like MetaMask, adhere to strict communication protocols—including never asking for Secret Recovery Phrases—can aid in identifying illegitimate communications. This heightened awareness not only reduces the risk of falling victim to malicious tactics but also fortifies overall wallet security. The more informed users are, the less likely they are to inadvertently enable phishing attacks, thereby enhancing the integrity of the entire blockchain ecosystem.
Revoking Contract Approvals: A Critical Step
Revoking contract approvals can be a crucial step in mitigating the impact of a phishing attack. Following a security incident where a wallet may have been compromised through unauthorized contract permissions, acting swiftly to revoke these approvals can prevent further losses. MetaMask has integrated features allowing users to view these approvals directly from their portfolio, providing an easy avenue for wallet holders to manage their security settings proactively.
Additionally, resources like Etherscan and Revoke.cash offer straightforward processes for users to manually disconnect and revoke permissions for specific ERC tokens. Understanding the difference between contract approval compromise and full seed phrase exposure is vital; where approvals can be revoked, potentially allowing the user to retain their remaining assets, a compromised seed phrase necessitates abandoning the wallet altogether. This capability to revoke approvals equips users with options to respond effectively and safeguard their crypto assets.
Enhancing Security with Documentation and Tools
Enhancing security measures through comprehensive documentation and tools is fundamental for anyone engaging in cryptocurrency transactions. MetaMask’s security documentation specifically outlines critical practices to avoid falling victim to phishing attacks, including recognizing official sender domains, adhering to protocols regarding unsolicited communications, and understanding how to verify transactions. Such resources serve as vital references that empower users to make informed decisions when managing their wallets.
The availability of additional security tools further supports users in reinforcing their defenses against phishing scams. Utilizing extensions that provide automatic alerts for suspicious transactions or employing hardware wallets for larger holdings serves as an active deterrent against potential attacks. With the rapidly evolving threat landscape, staying well-versed in best practices through updated security documentation enables users to navigate the complexities of crypto wallet safety more effectively.
Building a Multi-Tier Security Model
Building a multi-tier security model is an effective strategy to further enhance crypto wallet protection. This approach involves diversifying holdings across various wallet types to minimize vulnerabilities. For example, using cold storage for long-term investments while reserving hot wallets for daily transactions serves to compartmentalize risk. By adopting a structured system where the bulk of assets are insulated from immediate access, users decrease their overall exposure to potential phishing incidents.
Implementing a multi-tier security model also includes training oneself to be cautious of unsolicited communications and proactively managing wallet permissions. The practice of regularly reviewing and adjusting approvals based on transaction patterns supports a defensive posture against potential attacks. Ultimately, this model not only provides a safety net for users against loss but also instills a culture of awareness towards personal crypto security.
Leveraging Hardware Wallets for Long-Term Holdings
Leveraging hardware wallets is an essential tactic for securing long-term cryptocurrency holdings. Unlike software wallets that are generally more susceptible to phishing attacks, hardware wallets store private keys offline and provide a robust defense against unauthorized access. By utilizing hardware wallets for substantial assets, users significantly decrease their risk profile, as these devices require physical possession and user authorization for transactions.
Furthermore, integrating hardware wallets within a broader security strategy—including regular phishing awareness practices and wallet management techniques—can create a formidable barrier against potential threats. Hardware wallets not only enhance security but also instill confidence in users, empowering them to store their crypto assets with greater peace of mind. The combination of these advanced security measures is critical in navigating the complexities of digital assets.
Addressing User Responsibility in Cryptocurrency
Addressing user responsibility in the cryptocurrency landscape is crucial for improving overall security. While wallet providers can implement anti-phishing tools and offer guidelines for safe practices, the onus ultimately falls on users to remain vigilant. Recognizing that the self-custodial nature of cryptocurrency introduces unique risks reinforces the importance of personal accountability when managing digital assets. Understanding the need for proactive security measures enables users to participate actively in safeguarding their investments.
Moreover, the growing prevalence of phishing incidents serves as a reminder of the potential consequences of negligence. Educating oneself on security threats and adopting preventative measures becomes vital in a landscape where attackers continuously adapt their tactics. Taking personal responsibility for security not only benefits individual users but contributes to building a more robust and secure ecosystem for everyone involved in cryptocurrency.
Future Trends in Crypto Security and User Education
Future trends in crypto security emphasize the integration of advanced technology and user education as critical defenses against evolving threats. As the crypto landscape becomes increasingly complex, so too do the methods employed by attackers. Future innovations may include enhanced verification processes, use of biometric data for authorizing transactions, and automated systems for detecting suspicious activity. Keeping pace with these innovations is imperative for users to maintain secure wallets.
Equally important is the role of continued user education in fostering a safer cryptocurrency environment. Interactive learning modules, community engagement, and frequent updates on emerging threats must become standard practice. As both technology and user behavior evolve, creating a partnership between crypto providers and users focused on education and adaptation will be essential for combating phishing scams and ensuring safe crypto wallet utilization.
Frequently Asked Questions
What are common phishing scams targeting MetaMask users?
Phishing scams targeting MetaMask users often involve fraudulent emails that impersonate official communications. These emails might claim that a mandatory MetaMask upgrade is needed or request users to verify their account information. A common tactic is to include the MetaMask logo and misleading sender names, creating a sense of urgency that encourages users to click on malicious links.
How can I protect my crypto wallet from MetaMask phishing attempts?
To protect your crypto wallet from MetaMask phishing attempts, always verify sender email addresses, avoid clicking on unsolicited links, and never provide your Secret Recovery Phrase. Use official MetaMask channels for upgrades and support. Additionally, consider setting spending caps on token approvals and regularly reviewing your wallet’s security settings.
What should I do if I accidentally clicked a phishing link related to MetaMask?
If you accidentally clicked a phishing link related to MetaMask, immediately revoke any approvals made by your wallet. Use the MetaMask Portfolio or Revoke.cash to review and revoke token permissions. Additionally, check for any unauthorized transactions and consider creating a new wallet to move any remaining assets. Treat your original seed phrase as compromised.
What steps can I take to identify MetaMask phishing emails?
To identify MetaMask phishing emails, look for signs such as mismatched sender addresses, grammatical errors, urgent language requesting updates that MetaMask never issues, and suspicious URLs that do not match the official MetaMask domain. Always hover over links before clicking to verify their destination.
What are some wallet protection tips to avoid MetaMask phishing scams?
Some wallet protection tips to avoid MetaMask phishing scams include using a hardware wallet for significant holdings, enabling transaction security alerts, diversifying your wallets to limit exposure, and regularly reviewing contract approvals. Additionally, maintain a healthy skepticism toward unsolicited emails from any wallet provider.
How can I revoke token approvals to prevent MetaMask phishing attacks?
You can revoke token approvals to prevent MetaMask phishing attacks by using the MetaMask Portfolio or tools like Revoke.cash. Connect your wallet, review the list of active approvals by network, and send revocation transactions for any untrusted contracts to prevent unauthorized access.
What risks do phishing attacks pose to my MetaMask wallet?
Phishing attacks can lead to unauthorized access and theft of assets from your MetaMask wallet. These attacks often allow scammers to execute transactions or drain funds if you’ve clicked malicious links and granted them permissions. It’s crucial to take preventive measures and act quickly if you suspect a breach.
How can I stay updated on MetaMask security best practices?
To stay updated on MetaMask security best practices, regularly check the official MetaMask blog, follow security updates on their social media channels, and engage with community discussions in crypto forums. Awareness of the latest phishing methods and security features can significantly enhance your wallet’s protection.
| Key Point | Details |
|---|---|
| Phishing Email Tactics | Emails disguised as mandatory updates trick users into revealing sensitive information, utilizing familiar branding and urgent messaging. |
| Current Situation | $107,000 has been drained from multiple wallets, with attackers capitalizing on holiday distractions. |
| Detection Indicators | Check for mismatched sender names, suspicious URLs, and requests for sensitive information to identify phishing attempts. |
| Mitigation Strategies | Users should revoke token approvals, use hardware wallets, and maintain separate wallets to enhance security. |
| Historical Context | Despite security measures, personal wallet losses increased markedly, reflecting user vulnerability. |
Summary
MetaMask phishing is a rising threat that exploits user naivety through sophisticated email scams. As detailed, hundreds of wallets have been compromised, leading to significant financial losses. Understanding how to spot phishing attempts and implement defensive strategies is crucial for protecting digital assets. Regularly reviewing transactions, revoking unnecessary approvals, and utilizing secure practices can help mitigate risks and safeguard against these types of attacks.