The MetaMask phishing scam has become a pressing concern for cryptocurrency users looking to safeguard their digital assets. This evolving threat targets unsuspecting individuals by mimicking the interface of the popular wallet, leading them through a deceptive two-factor authentication (2FA) process. As phishing scams continue to rise, it’s crucial for users to understand the intricacies of how these attackers operate, specifically in the context of MetaMask security. With the sophistication of these cryptocurrency scams, even experienced users can fall prey to the elaborate designs crafted by cybercriminals. By staying informed about these risks, users can better protect themselves from falling victim to crypto phishing schemes that threaten their financial security.
In recent times, a troubling trend has emerged, with various schemes targeting users of digital wallets through deceptive practices. Specifically, fraudsters have turned to social engineering tactics that leverage familiar interfaces to trick users into revealing sensitive information. The prevalence of fake verification processes, particularly those associated with well-known crypto platforms, poses significant risks to users’ assets. This alarming development underscores the urgent need for heightened awareness about the evolving landscape of digital scams. As individuals increasingly rely on cryptocurrency for transactions, understanding and identifying security threats becomes paramount to safeguarding personal finances.
Understanding the MetaMask Phishing Scam
The rise of digital currencies has unfortunately accompanied a surge in phishing scams, particularly targeting cryptocurrency wallets like MetaMask. The MetaMask phishing scam utilizes sophisticated techniques, most notably counterfeit two-factor authentication (2FA) prompts that can easily deceive even experienced users. This trend of crypto phishing exploits the trust users have in familiar platforms, highlighting the need for enhanced awareness in the crypto community. As phishing tactics continue to evolve, users must remain vigilant against these increasingly sophisticated threats.
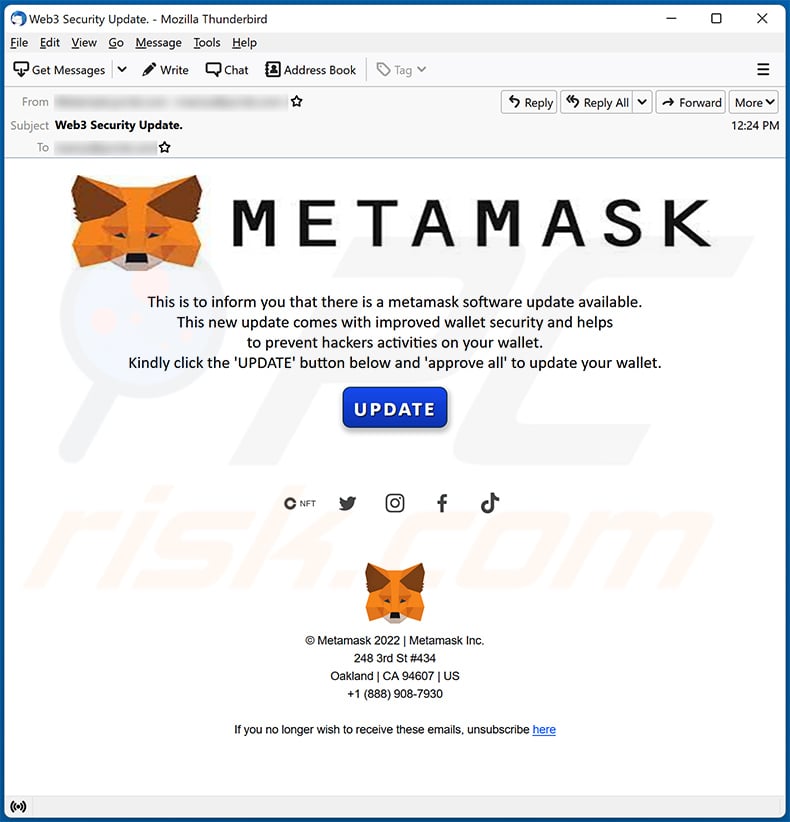
Typically, this phishing campaign manifests as an email that appears to come from MetaMask Support. It instructs users to activate mandatory 2FA, relying on brand logos and design elements that mirror the legitimate MetaMask platform. Such polished designs can easily lead to confusion, especially for those who might be casually checking their emails on mobile devices. Understanding the components of these scams and their operational techniques is crucial for safeguarding cryptocurrency assets, as one wrong click could lead to devastating financial losses.
How 2FA is Exploited in Phishing Attacks
Two-factor authentication is often hailed as a strong security feature, but in cases of phishing scams, it can be weaponized against users. In the MetaMask phishing scam, attackers frame the request for seed phrases as part of a mandatory security upgrade, exploiting the sense of urgency that accompanies such notifications. This manipulation of human psychology makes two-factor authentication a double-edged sword, where its legitimacy can lure users into giving away their most sensitive information.
Once victims are redirected to a phishing site that mimics the MetaMask interface, they are led through a series of seemingly legitimate steps designed to reinforce the illusion of security. The final deception occurs when individuals are prompted to enter their wallet seed phrase, supposedly to complete the 2FA setup. By understanding the methods employed in these attacks, cryptocurrency users can better protect themselves from falling victim to such scams. This awareness not only helps in avoiding phishing attempts but also underscores the importance of treating security notifications with a healthy degree of skepticism.
The Evolving Landscape of Cryptocurrency Scams
As cryptocurrency popularity increases, so does the sophistication of phishing scams targeting users. In recent years, there has been a significant evolution in how these scams operate, shifting from simplistic spam messages to more intricate and convincing impersonations. The MetaMask phishing scam exemplifies this trend, employing well-designed emails and convincing web domains that closely resemble genuine MetaMask communications. With attackers becoming savvier, the threat landscape demands that users stay informed about the tactics employed in cryptocurrency scams.
The overall reduction in cryptocurrency phishing losses does not indicate that the threat is diminishing; rather, it shows that scammers are investing more in the quality of their attacks. As observed in 2026, renewed market activity can trigger a comeback of phishing schemes, emphasizing the need for cryptocurrency enthusiasts to remain alert. Understanding common features of these scams, including how attackers blend legitimate branding with social engineering tactics, is vital for protecting one’s assets.
Recognizing the Signs of Phishing Scams
Recognizing the signs of a phony email or website is crucial in safeguarding against phishing scams like the MetaMask attack. For instance, scrutinizing the sender’s email address can reveal subtle discrepancies, such as a misspelled domain that looks similar to the legitimate one. As attackers often go to great lengths to ensure their communication mimics that of trusted organizations, becoming familiar with the legitimate branding and communication styles of platforms like MetaMask is essential.
Additionally, users should be cautious of any unsolicited requests for sensitive information, especially concerning their wallet seed phrases or recovery information. True crypto wallet providers will never ask for this information via email or through unsolicited prompts. Developing a habit of verifying requests through official channels can significantly reduce the risk of falling victim to phishing scams. Awareness and proactive measures are key to thwarting these increasingly sophisticated attacks.
Protecting Your Crypto Assets from Phishing
Protecting your cryptocurrency assets from phishing scams requires a multi-faceted approach. First and foremost, ensure you’re using strong, unique passwords for your wallets, combined with reliable two-factor authentication methods. This additional layer of security can deter unauthorized access, even if a phishing attack is attempted. Be cautious of communications that urge you to make immediate changes to your account settings or provide sensitive information under pressure.
Moreover, regularly educating yourself about the latest phishing tactics can further bolster your defenses. Awareness of how scammers manipulate social engineering and exploit genuine features, such as 2FA, can empower users to question requests before acting on them. Opt for security tools and protections offered by wallet providers. Ultimately, the best defense against phishing scams is a well-informed and skeptical approach to security.
The Importance of MetaMask Security Practices
Given the prevalence of MetaMask phishing scams, implementing rigorous security practices has never been more important. Users must educate themselves on the vulnerabilities associated with crypto wallets, particularly how seed phrases function and the implications of sharing them. Best practices include storing seed phrases securely offline and ensuring they are never entered on any website other than the legitimate MetaMask service.
Furthermore, engaging in regular security audits of your own practices is beneficial. Periodically reviewing your account’s security settings and educating yourself about common phishing strategies can help you stay ahead of potential threats. Crypto security is ultimately a personal responsibility, and attentive users will fair better against the growing number of cryptocurrency scams.
Two-Factor Authentication: A Double-Edged Sword
Two-factor authentication (2FA) is widely perceived as a fundamental security measure to protect digital assets, but it also has the potential to facilitate scams when misused. In the context of the MetaMask phishing scam, attackers cleverly exploit the trust associated with 2FA prompts to coax users into disclosing wallet seed phrases. With many individuals under the impression that 2FA represents a ‘fail-safe’ security feature, the psychological manipulation becomes particularly effective.
This alarming trend necessitates a shift in how users perceive 2FA within the cryptocurrency ecosystem. While it adds a necessary layer of security, it shouldn’t be relied upon as the sole method of protection. Users are encouraged to complement 2FA with additional layers of defense, such as hardware wallets and cautious verification of all requests for sensitive information. Recognizing the dual role of 2FA will empower users to safeguard their crypto assets more effectively.
Identifying Counterfeit Emails and Websites
Users’ ability to identify counterfeit emails and websites can significantly reduce susceptibility to phishing scams like those targeting MetaMask. For example, examining the source of an email can reveal red flags such as unusual sender addresses that may mimic legitimate domains. Additionally, scrutinizing hyperlinks within emails is crucial, as many phishing attempts disguise malicious links as safe URLs.
In cases where users land on suspicious websites, inspecting the URL for relevant indicators of authenticity—like SSL certifications or official brand markers—can also be revealing. Empowering users with the knowledge to discern authentic communications from counterfeit attempts is vital in the ongoing battle against crypto phishing. By recognizing these indicators, users can better protect their assets from nefarious schemes.
Staying Informed: The Key to Crypto Security
Staying informed about emerging threats is essential for any cryptocurrency user. As scams like the MetaMask phishing attempt illustrate, attackers continuously refine their strategies and methodologies. Regularly reviewing the latest information from trusted sources can provide insights into the evolving landscape of phishing tactics and trends within the cryptocurrency space. Awareness of changes can help users better anticipate potential risks.
Additionally, engaging with community discussions can better equip individuals with real-time knowledge and experiences shared by others. Participating in forums that focus on cryptocurrency security can enhance understanding and awareness of best practices. By fostering a culture of informed vigilance, users create a proactive environment aimed at mitigating the risks posed by phishing attacks and other cryptocurrency scams.
Frequently Asked Questions
What is the MetaMask phishing scam and how does it work?
The MetaMask phishing scam involves sophisticated tactics to trick users into disclosing sensitive information, such as wallet recovery phrases. Attackers send fake emails that appear to be from MetaMask Support, urging users to enable two-factor authentication. These emails mimic MetaMask branding closely and direct users to counterfeit websites that look similar to the genuine MetaMask interface. During the scam, users are prompted to enter their wallet seed phrase, enabling attackers to gain full access to their cryptocurrency holdings.
How can I identify a MetaMask phishing scam email?
To identify a MetaMask phishing scam email, look for subtle discrepancies in the sender’s address, as the counterfeit domains can differ by just a single character from the legitimate MetaMask domain. Be wary of emails requesting personal information or urging immediate action to enable 2FA. If the message claims to be from MetaMask Support but contains spelling errors or grammatical mistakes, it is likely a phishing attempt. Always verify links by hovering over them to see the actual URL before clicking.
What steps can I take to protect myself from MetaMask phishing scams?
To protect yourself from MetaMask phishing scams, avoid clicking on links in unsolicited emails. Always navigate to MetaMask directly by typing the URL into your browser. Enable security measures such as two-factor authentication where applicable, and use hardware wallets for added protection. Keep your wallet recovery phrase confidential and never share it with anyone, including supposed technical support representatives.
What should I do if I think I have fallen victim to a MetaMask phishing scam?
If you suspect you’ve fallen victim to a MetaMask phishing scam, immediately revoke access to any suspicious sites from your wallet. Transfer your assets to a new wallet with a different recovery phrase. Report the phishing site to MetaMask and monitor your accounts for unauthorized transactions. Additionally, changing passwords and enabling security measures like 2FA on a legitimate platform is essential for enhanced protection going forward.
Are cryptocurrency scams like MetaMask phishing becoming more sophisticated?
Yes, cryptocurrency scams, including the MetaMask phishing scam, are becoming increasingly sophisticated. Attackers are employing refined social engineering techniques that involve polished designs and convincing impersonations to deceive users. The use of recognizable branding and intricate web interfaces makes these scams harder to detect, emphasizing the need for constant vigilance among crypto users.
How does two-factor authentication (2FA) factor into MetaMask phishing scams?
In MetaMask phishing scams, two-factor authentication (2FA) is used as bait. Scammers create a sense of urgency for users to enable 2FA, convincing them that it enhances security. This sophistication deceives users into believing they are taking preventive measures when, in reality, they are inputting their sensitive recovery phrases into a fake platform, thus compromising their wallets.
| Key Points | Details |
|---|---|
| Fake MetaMask 2FA Phishing Scam | A sophisticated phishing campaign targeting MetaMask users that exploits counterfeit 2FA checks to steal wallet access. |
| Method of Operation | The scam impersonates MetaMask Support, using emails that mimic official correspondence and designed to look legitimate, including the blockchain provider’s branding and logos. |
| Phishing Site Features | The phishing site closely resembles the real MetaMask interface, tricking users into believing they are within a secure environment. |
| Final Step of Scam | Users are prompted to enter their wallet seed phrase under the guise of completing 2FA setup, which enables the attacker to access their wallet. |
| Risks and Awareness | Even experienced users can fall for the scam due to the use of familiar security features like 2FA, which adds a layer of credibility to the deception. |
| Security Recommendations | Users should never disclose their recovery phrases and remain vigilant against such scams, especially as crypto market activity increases. |
Summary
The MetaMask phishing scam highlights the alarming trend of sophisticated phishing attacks targeting cryptocurrency users. As scammers increasingly refine their tactics by utilizing counterfeit two-factor authentication processes and mimicking legitimate services, the risk for users continues to grow. Understanding these threats and adhering to recommended security practices is critical to safeguarding one’s crypto assets.