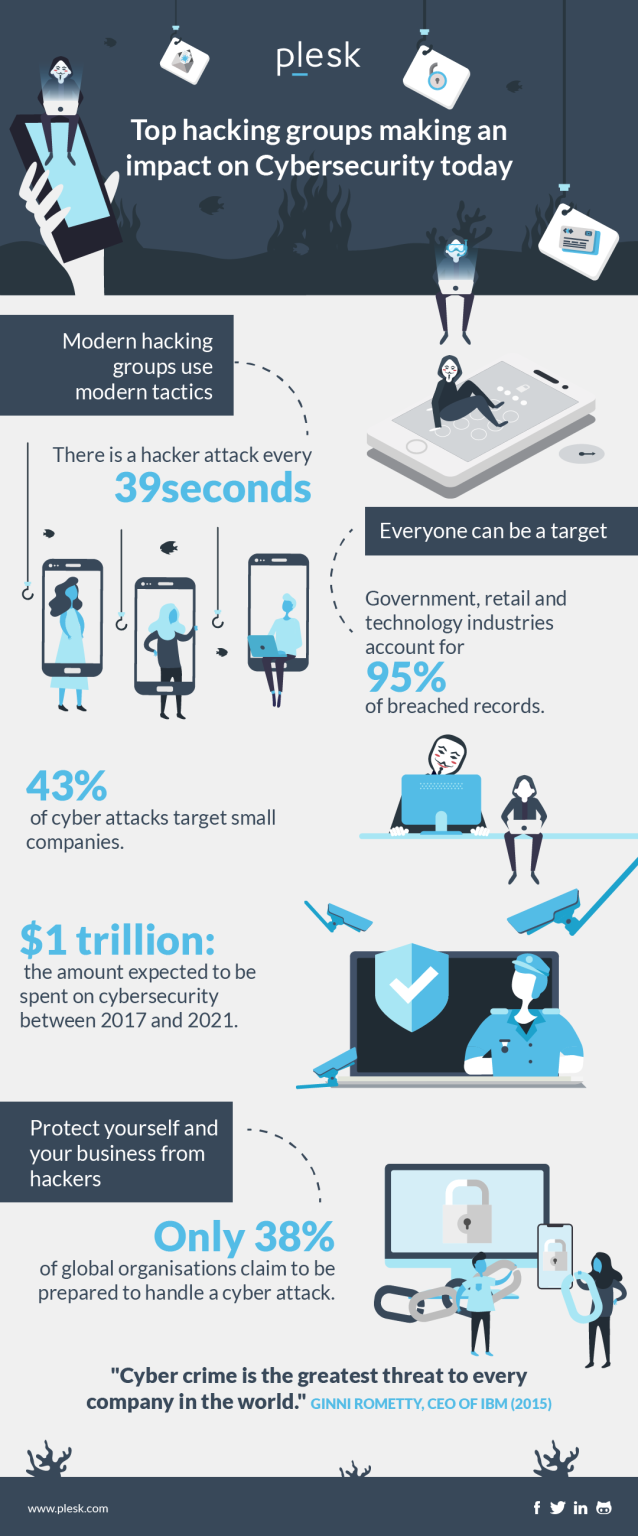
Hacking organizations have become increasingly sophisticated in their operations, often employing advanced tactics to infiltrate networks and exploit vulnerabilities. These groups utilize innovative worm propagation techniques to distribute malware, enabling them to access sensitive information with alarming efficiency. One common strategy involves the use of fake Zoom meetings, luring unsuspecting victims into a false sense of security while ultimately compromising their devices. Additionally, these organizations often prioritize Telegram account security by targeting users and infecting their contacts through malicious links and compromised applications. As cybersecurity threats continue to evolve, the need for heightened awareness and proactive measures has never been more critical.
Cybercriminal groups, also referred to as hacking collectives or malicious entities, are increasingly leveraging technology to carry out their illicit activities. These entities employ various strategies, including deceptive online communications and aggressive malware deployment, to achieve their goals. They often initiate attacks by manipulating unsuspecting users into engaging with fake video conferences or, more subtly, by infiltrating messaging platforms like Telegram. These operations not only compromise individual accounts but also lead to a cascading effect of infection among the victim’s contacts. Understanding the evolving landscape of such cyber threats is vital for users seeking to bolster their online defenses.
| Key Points | Details |
|---|---|
| Hacking organizations using worm propagation | Certain hacking organizations are employing worm propagation techniques to spread malware effectively. |
| Accessing Telegram accounts | Hackers gain access to Telegram accounts to contact the victim’s friends and relatives. |
| Multi-language operation | The hacking organizations communicate in both Chinese and English to reach a wider audience. |
| Methods of infection | Common methods include fake Zoom calls, poisoned code repositories, or compromised third-party tools and games. |
| Theft operations | After successfully infecting their targets, hackers steal cryptocurrencies and account information. |
| Continuous optimization | Hacking organizations consistently refine their worm propagation techniques to increase effectiveness. |
Summary
Hacking organizations are increasingly utilizing sophisticated techniques to exploit vulnerabilities and spread malware through worm propagation engineering. This evolving threat landscape requires heightened awareness and proactive measures to protect against these malicious activities.
Understanding Hacking Organizations and Their Tactics
Hacking organizations have become increasingly sophisticated in their methods of exploiting vulnerabilities in digital systems. One of the most alarming trends is their use of worm propagation techniques to spread malware rapidly across networks. By infiltrating various platforms, these organizations can exploit user permissions, especially on messaging apps like Telegram, to launch targeted attacks. The implications for private users and businesses alike are significant, as these hackers often utilize their access to not only steal sensitive information but also to spread malware to the contacts of their victims.
These organizations don’t just operate in isolation; they leverage social engineering tactics to maximize their reach. For instance, they may initiate fake Zoom meetings impersonating a trustworthy source, drawing unsuspecting targets into a trap. This breach of trust is then expanded to other contacts, perpetuating the cycle of infection as the malicious code propagates. Affected users may find their own accounts compromised, leading to a cascade of security breaches that can devastate their personal and professional lives.
The Role of Worm Propagation Techniques in Cybersecurity Threats
Worm propagation techniques are central to the strategies employed by hacking organizations. These techniques allow malware to replicate itself and spread without user intervention, effectively creating a self-sustaining infection cycle. As organizations continuously refine these methods, the threats they pose evolve as well, becoming more resilient against conventional cybersecurity measures. The use of such techniques highlights the importance of adaptive defense strategies within the realm of cybersecurity.
By understanding worm propagation mechanisms, cybersecurity professionals can better prepare for and mitigate these threats. This includes regular evaluation of software permissions and user access to communication tools like Telegram, which are often exploited during attacks. Educating users about the risks associated with compromised tools, such as fake applications or poisoned code repositories, can significantly reduce the effectiveness of these propagation tactics, keeping personal and organizational data safer.
Securing Your Telegram Account Against Hacking Attempts
Given the rise of hacking organizations leveraging Telegram for their attacks, it’s essential to prioritize security on this messaging platform. One effective measure is to enable two-factor authentication (2FA) on your account, providing an extra layer of protection that makes unauthorized access significantly more difficult. Regularly updating your password and ensuring it is unique can also prevent hackers from easily accessing your account.
In addition to personal security measures, be cautious with the messages you receive. Many hackers try to deceive users by sending links or invitations to fake Zoom meetings under the guise of legitimate interactions. Always verify the authenticity of such invitations and avoid clicking on suspicious links that may lead to phishing sites or infect your device with malware. These small but critical steps can help safeguard your account from hacking organizations and enhance your overall online security.
The Dangers of Fake Zoom Meetings in Cyber Attacks
Fake Zoom meetings have become a common tool used by cybercriminals as a means to gain access to sensitive information. These meetings can appear legitimate, often involving impersonated individuals or organizations that encourage users to provide personal data. As the number of remote interactions continues to rise, hackers have perfected this tactic to exploit the trust inherent in virtual environments.
Participants in these meetings are often lured into sharing confidential information or clicking on compromised links. Once an account is breached, hackers can then utilize worm propagation techniques to infect the contacts of the affected user, creating a snowball effect of compromised accounts. Understanding these tactics is crucial for individuals and organizations alike to mitigate potential risks associated with fake Zoom meetings.
Infecting Contacts: A Strategy of Cybercriminals
Infecting contacts is a strategic approach employed by many hacking organizations to expand their reach and amplify the impacts of their cyber attacks. Once a hacker gains access to a user’s account, especially through platforms like Telegram, they can easily spread malware to the contact list without the original user’s knowledge. This method leverages the inherent trust that exists within social circles, making it more likely that contacts will engage with the malicious content.
This tactic demonstrates the critical need for awareness around the security of not only one’s own accounts but also the accounts of those in your network. Encouraging friends and family to practice good cybersecurity hygiene, such as avoiding suspicious links and employing strong passwords, can create a shield against the spread of malware. By fostering a culture of vigilance, individuals can help minimize the effectiveness of hacking organizations and their infecting strategies.
Proactive Measures Against Cybersecurity Threats
In the face of increasing cybersecurity threats, proactive measures are necessary to protect personal data and ensure digital safety. This includes regularly updating software and applications to patch any vulnerabilities that hackers might exploit. Additionally, utilizing comprehensive security solutions, such as anti-malware tools, can detect and neutralize threats before they escalate.
It is also essential to educate oneself about the latest cyber threats and hacking techniques. Understanding how organizations utilize worm propagation and social engineering tactics allows users to remain vigilant against potential attacks. Regular training and awareness programs can empower users to recognize suspicious behavior, ensuring everyone is informed and prepared to react appropriately to minimize risks.
The Evolution of Cybersecurity Compliance
As hacking organizations innovate, so too must the frameworks governing cybersecurity compliance evolve. Laws and regulations surrounding data protection are becoming more stringent, pushing organizations to adopt more rigorous security protocols. Compliance not only protects sensitive information but also instills trust among users who are increasingly wary of cyber threats.
Organizations must adopt a proactive stance toward compliance by integrating advanced security practices that align with regulatory guidelines. This includes thorough audits of existing security measures, regular training for employees, and a commitment to transparency regarding data handling practices. By prioritizing compliance in an ever-changing threat landscape, organizations can bolster their defenses and mitigate risks associated with cyber attacks.
Navigating the Threat Landscape: Key Takeaways
Navigating the threat landscape requires a multifaceted approach that considers the various tactics employed by hacking organizations. Awareness of the latest methods used for worm propagation and social engineering is paramount in developing effective cybersecurity strategies. Users should remain vigilant and proactive about their online footprint, ensuring that they are protected against evolving threats.
Moreover, organizations must foster a culture of cybersecurity, where awareness and training are part of the organizational fabric. This not only enhances individual preparedness but also strengthens the collective resilience against cyber threats. By working together and prioritizing security, users and organizations alike can withstand the persistent challenges posed by hacking organizations.
Frequently Asked Questions
What are hacking organizations doing with worm propagation techniques?
Hacking organizations are increasingly using worm propagation techniques to spread malware across networks. By exploiting vulnerabilities, they can gain access to users’ devices and accounts, facilitating the theft of sensitive information and assets.
How are fake Zoom meetings being used by hacking organizations?
Hacking organizations employ fake Zoom meetings to lure unsuspecting victims into sharing sensitive information. These scams take advantage of users’ trust in popular communication platforms to execute phishing attacks and deploy malware.
What role does Telegram account security play in the operations of hacking organizations?
Telegram account security is critical, as hacking organizations often target these accounts. Once they obtain permissions, they can infiltrate users’ contact lists, spreading malware and phishing scams efficiently among friends and colleagues.
How do hacking organizations infect contacts through social engineering?
Hacking organizations utilize social engineering strategies, like impersonating trusted contacts, to infect their victims. They may leverage compromised applications, such as fake Zoom meetings and social media channels, to deceive users into downloading malicious software.
What are some common cybersecurity threats related to hacking organizations?
Common cybersecurity threats from hacking organizations include phishing attacks, malware infections through worm propagation techniques, fake communications on platforms like Zoom and Telegram, and exploitation of vulnerable software or games.
How can individuals protect themselves from phishing attacks by hacking organizations?
To protect against phishing attacks, individuals should implement strong security measures like enabling two-factor authentication on their Telegram accounts, being cautious of unverified communications, and avoiding clicking links in suspicious emails or messages.