| Key Point | Details |
|---|---|
| Surge in Activity | Recent surge in Ethereum’s activity is linked to address dusting attacks. |
| New Addresses | 2.7 million new addresses were created, representing a 170% increase from normal levels. |
| Transaction Volume | Daily transaction volume exceeded 2.5 million. |
| Fusaka Upgrade Impact | The Fusaka network upgrade in December cut transaction fees by over 60%. |
| Dust Asset Recipients | 3.8 million addresses have received dust assets, accounting for 67% of new addresses. |
| Victims & Losses | 116 victims have reported losses exceeding $740,000 due to dusting attacks. |
Summary
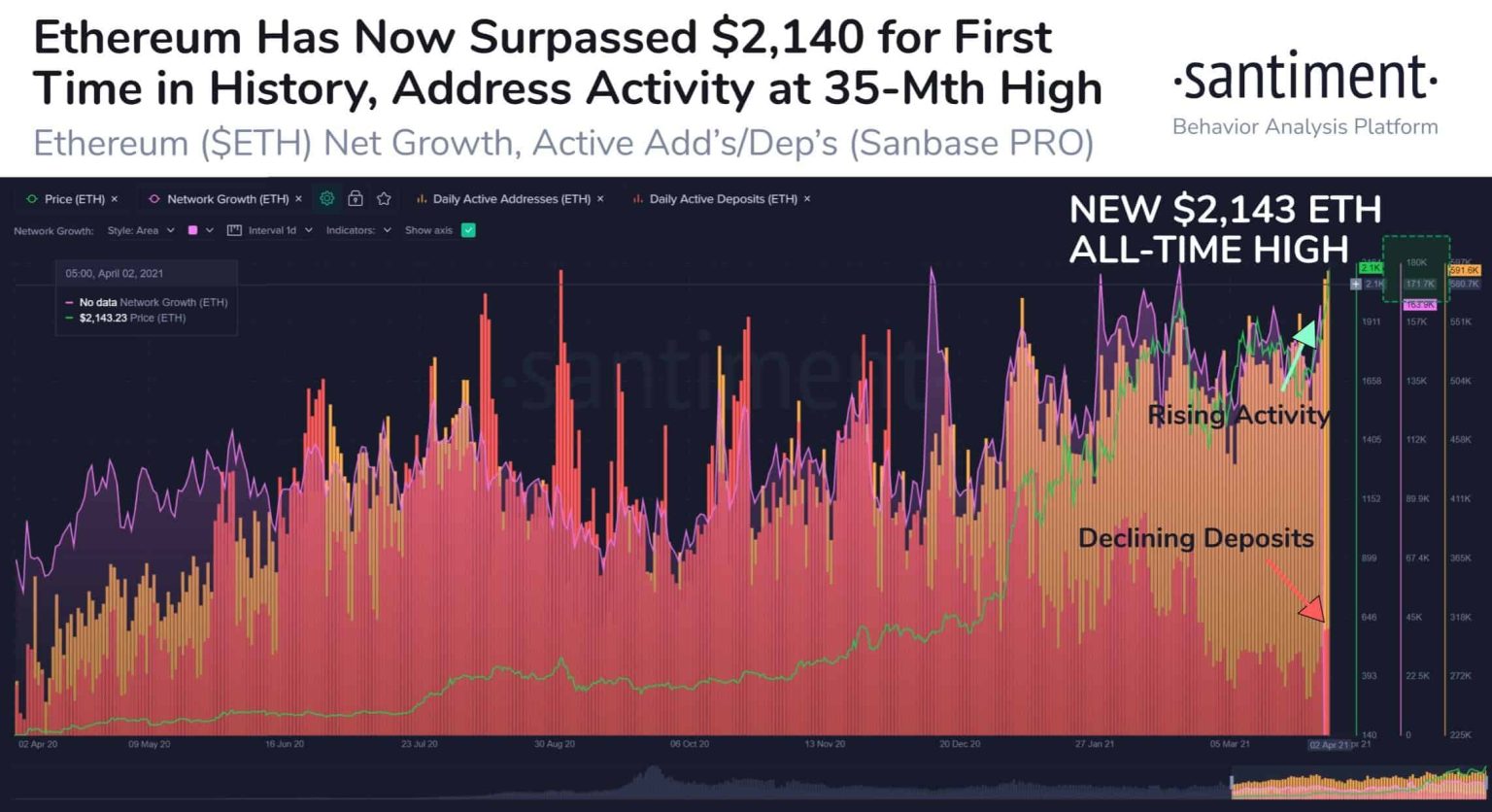
Ethereum network activity has surged significantly due to the prevalence of address dusting attacks utilizing low gas fees. The recent data highlights a remarkable growth in new addresses and increased transaction volumes, all coinciding with the decreased transaction costs following the Fusaka upgrade. As the network faces these challenges, understanding the implications of dusting attacks on Ethereum’s ecosystem is crucial for users and investors alike.
Ethereum network activity has witnessed a remarkable surge recently, primarily driven by a rise in address dusting attacks that exploit low gas fees. The week of January 12 displayed extraordinary figures, with 2.7 million new addresses created—an increase of 170% compared to typical activity. This unprecedented trend also saw daily cryptocurrency transaction volume soar past 2.5 million, indicative of the network’s heightened engagement. The introduction of the Fusaka network upgrade in December played a significant role, cutting transaction fees by over 60%, which inadvertently facilitated these large-scale spam tactics. Alarmingly, 3.8 million Ethereum addresses have been impacted, with 116 of these victims incurring losses aggregating to over $740,000 due to the dusting phenomenon.
The Ethereum blockchain, known for its robust activity, has recently experienced a notable uptick, correlating with malicious practices such as address dusting schemes. Following the implementation of a significant protocol upgrade, users have noted a considerable reduction in transaction costs, prompting an influx of new wallet creations. This escalation in address creation and transaction frequency directly links to a rise in bad actors targeting network vulnerabilities. Meanwhile, the overall volume of transactions within the Ethereum ecosystem has surged, attracting attention from both the cryptocurrency community and cybersecurity experts. As the landscape of digital assets evolves, understanding the implications of these trends is crucial for all Ethereum stakeholders.
Understanding Ethereum Network Activity
Ethereum network activity has seen a remarkable increase, primarily driven by various malicious strategies like address dusting attacks. During the recent surge, which occurred between January 12 and the following weeks, the Ethereum blockchain recorded an unprecedented number of new addresses. With 2.7 million new addresses being created, marking a staggering 170% rise from the average, it’s clear that attackers are capitalizing on the lowered transaction fees introduced by the Fusaka network upgrade. This upgrade significantly reduced Ethereum gas fees, making it economically favorable for bad actors to execute spam attacks without significant costs.
This increase in Ethereum network activity not only reflects the rise of dubious transactions, but it also poses a substantial risk to the integrity of the cryptocurrency ecosystem. The introduction of low-cost transactions has allowed more individuals to conduct trades and transfers; however, it has equally opened doors for malicious users. As 3.8 million addresses have already received dust assets, many unsuspecting users have become inadvertent victims of these attacks, with reports indicating losses exceeding $740,000. The necessity to monitor Ethereum transaction volume closely cannot be overstated as it serves as a barometer for both legitimate activity and potential fraud.
The Impact of Address Dusting Attacks on Ethereum
Address dusting attacks have emerged as a significant threat within the Ethereum landscape. They involve sending tiny amounts of cryptocurrency to a large number of wallet addresses, a tactic intended to compromise privacy and create confusion among users. As Ethereum experiences a surge in activity, the impact of these attacks becomes increasingly pronounced, particularly in light of the Fusaka network upgrade that has made such operations cheaper to execute. By reducing Ethereum gas fees by over 60%, the upgrade has inadvertently encouraged malicious players to engage in large-scale dusting, further eroding user confidence.
With 67% of the newly created addresses having been targeted with dust transactions, the repercussions of these attacks extend beyond mere financial loss. Users often face decreased security and privacy as their transaction histories become intertwined with dirtied asset flows. This rising trend of address dusting not only affects individual Ethereum addresses but also has broader implications for network integrity and user trust in the platform. Addressing the ramifications and enhancing security measures to combat dusting attacks is now more crucial than ever as Ethereum continues to grow.
The Role of the Fusaka Network Upgrade in Ethereum’s Activity
The Fusaka network upgrade has played a pivotal role in shaping ERC20 token transactions on Ethereum. By slashing transaction costs significantly, the upgrade has positioned Ethereum as an even more attractive platform for all types of users. However, this reduction in gas fees has had unintended consequences, as it has fueled an increase in the cryptocurrency transaction volume, largely attributable to spam attacks like address dusting. While the intention was to make Ethereum more accessible for decentralized applications (dApps) and everyday users, it has equally enhanced the capability of nefarious actors to exploit the network.
As Ethereum strives to maintain its position as the leading smart contract platform, the implications of the Fusaka network upgrade must be fully understood. Not only does this upgrade impact typical user transactions, it affects how the Ethereum addresses are targeted by bots and malicious software. Consequently, while the decrease in gas fees facilitates genuine transactions and fosters growth within the ecosystem, it simultaneously opens up new avenues that potentially compromise user safety and the legitimacy of the network. Balancing accessibility and security has become an urgent challenge for Ethereum moving forward.
Ethereum Gas Fees and Their Relation to Network Transactions
Ethereum gas fees serve as a significant cost factor that influences overall network usage and activity. These fees are essential for compensating miners who validate transactions on the blockchain and are pivotal for maintaining network efficiency. As seen during the recent spike in activity, reduced gas fees post-Fusaka upgrade have led to an influx in transaction volume and the emergence of various attack vectors such as address dusting. A lower cost per transaction invariably attracts more users but also opens doors for exploitative practices.
The continuous fluctuation of Ethereum gas fees directly correlates with the level of network demand. When fees are low, as they currently are, we witness a surge in activity that can stem from both legitimate use cases and malicious interactions. This duality urges users to remain vigilant of their transaction activities on Ethereum and the risks associated. In this context, the relationship between gas fees, network transactions, and overall security will remain a focal point as Ethereum evolves with its user base.
Risks Associated with High Ethereum Transaction Volume
High Ethereum transaction volumes, while reflecting robust network activity, come with inherent risks that cannot be overlooked. The surge in activity opens up pathways for attackers to exploit the system through practices like address dusting, where they aim to compromise users’ privacy and security. For victimized users, the consequences are serious, leading to financial losses and issues related to trust in the Ethereum platform. Moreover, such spikes in activity may lead to network congestion, further complicating transaction processing times and eventually affecting user experience.
To mitigate these risks associated with growing transaction volumes, users must adopt best practices such as securing their private keys and being cautious about engaging with unknown addresses or transactions. Furthermore, enhancing awareness about emerging threats related to Ethereum, like dusting attacks, is essential for fostering a secure environment. As scams become more sophisticated, the onus is on the community and developers to bolster defenses against such attacks, ensuring that the network can scale securely along with its user base.
Protecting Against Ethereum Dusting Attacks
As Ethereum users face the increasing likelihood of dusting attacks, understanding how to protect oneself becomes imperative. Dusting attacks aim to obfuscate transaction histories and compromise individuals’ privacy by sending negligible amounts of ETH to numerous addresses. For those involved in the Ethereum ecosystem, recognizing the signs of these attacks, such as sudden small transactions from unknown sources, can aid in avoiding social engineering traps where further financial loss may occur. Strategies such as using privacy-focused wallets or mixing services might also offer some protection against unwanted dusting.
In addition to individual measures, the broader Ethereum community needs to remain proactive in implementing protections against such patterns. The increased education surrounding these types of threats can enhance users’ awareness and readiness to counteract potential losses. Efforts to create decentralized applications that emphasize security and privacy can also help protect users from dusting attacks while contributing to a more secure overall network. Ultimately, the responsibility lies with both users and developers to foster an environment that mitigates risks and protects against the fallout from these malicious attacks.
Buying and Managing Ethereum Safely
Buying and managing Ethereum safely requires a diligent approach, especially as the network grapples with address dusting attacks and rising transaction volumes. Potential investors should familiarize themselves with secure platforms and wallets that prioritize user safety. When purchasing Ethereum, it’s crucial to utilize reputable exchanges that offer robust security protocols, including two-factor authentication and withdrawal whitelists. Staying informed about the latest developments in Ethereum’s ecosystem also plays a critical role in safeguarding one’s assets.
In addition to secure buying practices, effective management of Ethereum addresses is vital to prevent falling victim to dusting attacks. Users should regularly monitor their transaction history and be wary of unsolicited small transactions, as these may indicate a potential attack. Using dedicated wallets tailored for certain purposes, such as cold storage for long-term holdings, can enhance security. By implementing such practices, Ethereum users can navigate the cryptocurrency landscape more effectively and with greater confidence.
The Future Outlook for Ethereum’s Ecosystem
The future outlook for Ethereum’s ecosystem is poised to be dynamic yet complex, especially as it continues to experience significant activity and transaction volume increases. Innovations like the Fusaka network upgrade signal a drive toward enhancing Ethereum’s functionality but also introduce new challenges, such as increased exposure to address dusting attacks. As Ethereum strives for scalability and usability, maintaining a balance between growth and security will be vital for its long-term success.
Looking ahead, Ethereum may look to incorporate additional layers of security to combat emerging threats effectively. Initiatives aimed at developing better user awareness and protective measures against common attacks will be crucial in fostering a healthy ecosystem. Overall, Ethereum is at a pivotal juncture where its ability to adapt will determine how it shapes the future of blockchain technology and its acceptance among mainstream users.
Frequently Asked Questions
What are Ethereum dusting attacks and how do they affect network activity?
Ethereum dusting attacks refer to the practice where a small amount of cryptocurrency is sent to numerous Ethereum addresses. This technique is often used maliciously to track users’ wallets and potentially compromise their privacy. Such attacks have recently contributed to a surge in Ethereum network activity, as seen with the increase in new addresses and transaction volume.
How does the Fusaka network upgrade impact Ethereum transaction fees?
The Fusaka network upgrade, implemented in December, significantly reduced Ethereum transaction fees by over 60%. This reduction has encouraged more users to engage in transactions, thereby increasing Ethereum’s overall network activity, including instances of address dusting attacks that exploit these lower fees.
What is the recent trend in Ethereum transaction volume?
Recent data indicates that Ethereum transaction volume has surged, especially during the week of January 12, with daily transactions exceeding 2.5 million. This spike is partially attributed to address dusting attacks, which have become more frequent due to the lower transaction fees following the Fusaka network upgrade.
How many Ethereum addresses have been affected by dusting attacks?
Currently, approximately 3.8 million Ethereum addresses have received dust assets during these attacks. This figure represents about 67% of the newly created addresses, highlighting the significant impact of dusting attacks on Ethereum’s network activity.
What should victims of Ethereum dusting attacks expect in terms of financial losses?
Victims of Ethereum dusting attacks have reported losses totaling over $740,000 to date, with 116 individuals directly affected. These losses underscore the financial risks associated with increased network activity and the prevalence of such malicious tactics.