In the ever-evolving world of digital finance, the rise of Aave Ethereum LBTC phishing has brought to light significant vulnerabilities within the cryptocurrency ecosystem. Recently, a user fell victim to a sophisticated scam, losing 12 Aave Ethereum LBTC (aEthLBTC), equivalent to a staggering $1.08 million, by signing a malicious “license” signature. This incident underscores the dangers of cryptocurrency phishing, where unsuspecting users inadvertently compromise their assets. Experts like Slow Mist Yu Xian reveal that the phishing gang behind this attack is not one of the well-known threats, further complicating the landscape of ETH laundering and hacking. After executing their scheme, the attackers swiftly converted the stolen funds to ETH, utilizing Tornado Cash to obscure their tracks and evade detection.
The recent Aave Ethereum LBTC phishing incident highlights a growing trend in cryptocurrency scams that exploit unsuspecting users’ trust. As the digital asset space matures, malicious entities increasingly deploy tactics like deceptive signatures that can lead to devastating financial losses. This particular case, where significant amounts of aEthLBTC were fraudulently acquired, shines a spotlight on the pressing need for robust security measures within decentralized finance. Not only did the perpetrators quickly transfer their ill-gotten gains into Ethereum, but they also laundered the funds using services like Tornado Cash, which has become synonymous with digital asset obfuscation. The involvement of lesser-known phishing groups complicates the situation, emphasizing the importance of vigilance and education in safeguarding against such threats.
Understanding Aave Ethereum LBTC Phishing Attacks
Aave Ethereum LBTC phishing attacks have become a significant concern within the cryptocurrency community, particularly given their potential to cause devastating financial losses. In a recent incident, a user lost 12 aEthLBTC, amounting to approximately $1.08 million, due to inadvertently signing a malicious ‘license’ signature. This points to the critical need for heightened awareness about phishing schemes targeting cryptocurrency holders, which leverage deceptive tactics to manipulate individuals into exposing their assets.
Phishing attacks are often perpetrated by deceptive actors who craft realistic-looking requests or documents that trick users into providing sensitive information or signing harmful transactions. This unfortunate event underscores the importance of exercising caution while interacting with unfamiliar requests in the cryptocurrency space. Users must remain vigilant and deploy robust security practices to safeguard their funds against such malicious tactics.
The Role of Tornado Cash in ETH Laundering
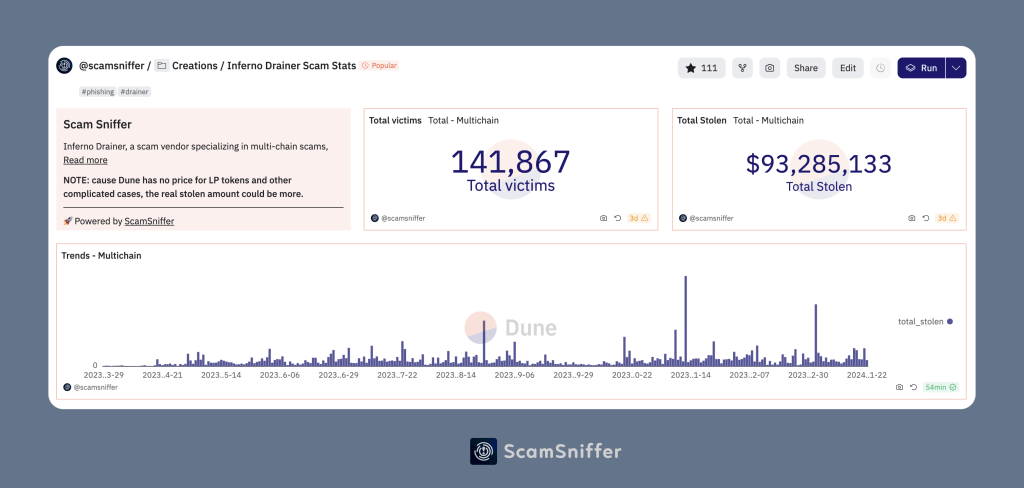
In the aftermath of phishing attacks like the recent Aave Ethereum LBTC incident, the stolen funds are frequently laundered to obscure their origins. Tornado Cash has emerged as a popular tool among criminals seeking to achieve this goal, providing a decentralized mixing service that enables users to anonymize their ETH transactions. After the phishing gang behind the attack quickly exchanged the stolen assets for ETH, they utilized Tornado Cash to obfuscate their tracks, making it difficult for law enforcement to trace the illicit gains.
The relationship between Tornado Cash and ETH laundering raises pressing questions about regulatory measures in the cryptocurrency realm. As decentralized finance continues to grow, the possibilities for concealing transactions have also expanded, highlighting the urgent need for frameworks to address illegal activities in this evolving landscape. By understanding how tools like Tornado Cash are exploited in the laundering process, stakeholders can better devise strategies to combat criminal activities in the cryptocurrency ecosystem.
Mitigating Risks of Aave Hacks and Phishing
To defend against the rising threat of Aave hacks and phishing scams, users must adopt a proactive approach to security. This involves familiarizing oneself with the warning signs of phishing attempts, such as unsolicited requests for wallet access or unusual transaction prompts. Utilizing multi-signature wallets and hardware wallets can further augment security, ensuring that private keys are stored offline and away from potential threats.
Moreover, education plays a critical role in mitigating risks associated with cryptocurrency phishing. By staying informed about the latest tactics used by malicious actors and participating in community discussions, users can arm themselves with knowledge that can significantly reduce their susceptibility to attacks. Engaging with resources that detail common phishing schemes can provide added layers of protection against the evolving nature of cryptocurrency-related scams.
Recognizing Malicious Signatures in Crypto Transactions
One of the key components of safeguarding assets in the cryptocurrency environment is the ability to recognize malicious signatures in transaction confirmations. Phishing attacks often succeed because victims do not scrutinize the permissions they grant to applications or transactions. Users must be educated on how to identify legitimate contracts versus those that may be designed to exploit them, particularly during busy trading periods when mistakes are more likely.
Being critical of the permissions requested by dApps and double-checking transaction details before signing can be crucial in avoiding scams. Tools that alert users to uncommon contract behaviors or automatic signature requests can help shield against potential fraud. Developing a habit of meticulous review can diminish the impact of phishing attempts, allowing users to enjoy the benefits of participation in the DeFi ecosystem safely.
The Impact of Phishing on Cryptocurrency Investment
Phishing attacks significantly undermine trust in the cryptocurrency market, creating a ripple effect that impacts investor sentiment and overall market stability. The recent loss of 12 Aave Ethereum LBTC exemplifies how individual incidents can collectively harm the reputation of blockchain projects and cryptocurrency exchanges. As malicious actors seek to exploit vulnerabilities, they not only directly rob investors but can also dissuade potential newcomers from engaging in the market.
To counteract the adverse effects of phishing, it is imperative for cryptocurrency platforms and stakeholders to implement robust security measures and educate users about potential risks. By cultivating a culture of security and transparency, the industry can work towards instilling confidence among users, thereby fostering a healthier investment landscape. As part of this effort, sharing insights and success stories about phishing prevention can empower users to take control of their financial security.
Trends in Cryptocurrency Phishing Attacks
The landscape of cryptocurrency phishing is continually evolving, with attackers developing increasingly sophisticated techniques to exploit unsuspecting users. Recent trends highlight a shift towards targeted phishing campaigns, where attackers focus on specific projects or platforms, such as Aave, to maximize their odds of success. This targeted approach often involves extensive research to make deceptive communications more believable, which necessitates a higher level of vigilance from prospective investors and users.
Additionally, the rise of decentralized finance (DeFi) and new token launches has opened new avenues for phishing attacks, as users scramble to follow the latest innovations and potentially lucrative investments. It is essential for individuals to maintain a critical perspective in such a fast-paced environment, continually reassessing the credibility of the platforms they engage with. Remaining alert to these trends will enhance users’ capacity to identify red flags and protect their investments.
The Future of Security in Cryptocurrency
As the cryptocurrency market continues to mature, so too does the imperative for advancing security protocols. The community is already witnessing innovative solutions designed to reduce the risks associated with phishing and scams, including smart contract audits and the incorporation of AI-driven security tools. By investing in cutting-edge technology and implementing best practices in cybersecurity, the industry can aim to create a more secure environment for all participants.
However, technological advancements alone will not sufficiency eliminate the threat of phishing. Continuous education and awareness campaigns targeting both novice and experienced users remain essential. These initiatives will help cultivate a culture of security mindfulness that recognizes the evolving tactics employed by attackers and prepares users to respond accordingly. In this rapidly changing landscape, fostering collaboration between developers, security experts, and the user community will be vital to establishing an increasingly resilient cryptocurrency ecosystem.
Case Study: The Aave Hack and Implications
The recent case of the Aave Ethereum LBTC hack serves as a poignant reminder of the vulnerabilities present in the cryptocurrency ecosystem. With a staggering loss of $1.08 million due to a simple yet deceptive phishing technique, this incident sheds light on the broader implications of security within DeFi platforms. Such cases not only affect individual investors but also create apprehension across the entire sector, raising the stakes for everyone involved.
Analyzing this case allows stakeholders to identify weaknesses in current security frameworks and better understand the behavior of malicious actors. Lessons drawn from this event should inform future policies and security practices within the cryptocurrency space. By establishing comprehensive safeguards and emphasizing education, the community can work collaboratively to minimize the risk of similar incidents, thereby enhancing the overall integrity of the market.
Protecting Your Assets in the Cryptocurrency Space
Protecting your cryptocurrency investments from phishing attacks requires a multi-faceted approach focused on education, technology, and personal vigilance. Users should regularly update their security knowledge, staying informed about the latest trends and tactics that scammers employ. Establishing strong passwords, enabling two-factor authentication, and considering hardware wallets are all steps toward fortifying personal security.
Moreover, fostering a sense of community can enhance protection against phishing. Engaging with forums, webinars, and local cryptocurrency groups can provide valuable insights into best practices for maintaining security. By sharing experiences and recommendations, users can learn from one another and develop a well-rounded approach to safeguarding their assets in this dynamic environment.
Frequently Asked Questions
What happened in the Aave Ethereum LBTC phishing incident?
In a recent Aave Ethereum LBTC phishing incident, a user lost 12 aEthLBTC after signing a malicious ‘license’ signature. This resulted in a significant loss of approximately $1.08 million.
How do attackers use phishing tactics in cryptocurrency like Aave Ethereum LBTC?
Attackers often employ cryptocurrency phishing tactics by sending fraudulent messages or links that trick users into signing malicious signatures. In the case of Aave Ethereum LBTC, the user was deceived into signing a harmful transaction that led to the loss of their funds.
What is the role of Tornado Cash in ETH laundering related to Aave hack incidents?
Tornado Cash is frequently used for laundering stolen cryptocurrency. In the recent Aave hack, the phishing gang rapidly exchanged the stolen funds for ETH and laundered them through Tornado Cash to obscure the transaction trail.
What should users do to protect themselves from Aave Ethereum LBTC phishing attacks?
To protect themselves from Aave Ethereum LBTC phishing attacks, users should be cautious when signing any transactions and verify the legitimacy of requests. Utilizing trusted wallets and enabling additional security measures can also help.
What are malicious signatures and how do they relate to Aave Ethereum LBTC phishing?
Malicious signatures are fraudulent transaction approvals that enable attackers to access user funds. In the Aave Ethereum LBTC phishing scenario, signing a malicious license signature led to substantial financial loss for the victim.
Why is it important to be aware of Aave hacks and phishing scams?
Being aware of Aave hacks and phishing scams is crucial for cryptocurrency users to avoid significant financial losses. Knowledge of common phishing tactics can help users secure their assets and identify potential threats.
How can I report an Aave Ethereum LBTC phishing attack?
If you encounter an Aave Ethereum LBTC phishing attack, report it to the appropriate cryptocurrency exchange or security organization. Additionally, informing communities about the phishing attempt can help others avoid similar losses.
| Point | Details |
|---|---|
| Incident | A user lost 12 Aave Ethereum LBTC (aEthLBTC) due to phishing. |
| Financial Loss | The loss amounted to approximately $1.08 million. |
| Phishing Group | The attackers are identified as a non-mainstream phishing gang. |
| Funds Laundering | Phishing proceeds were quickly exchanged for ETH and laundered using Tornado Cash. |
Summary
Aave Ethereum LBTC phishing represents a significant security threat in the crypto space, as demonstrated by a recent incident where a user lost a staggering 12 aEthLBTC, equating to roughly $1.08 million. This type of phishing attack involves misleading users into signing harmful contracts, showcasing the need for increased vigilance within the cryptocurrency community. The involvement of a lesser-known phishing gang highlights the evolving tactics employed by cybercriminals and underlines the importance of securing digital assets effectively.