In an age where connectivity is paramount, public WiFi security remains a crucial yet often overlooked aspect of our digital lives. Many individuals connect to open networks without a second thought, unaware of the lurking public WiFi risks that could jeopardize their personal and financial information. A stark reminder of this reality comes from a recent incident where a user lost $5,000 from a crypto wallet due to unsafe interactions over a hotel’s unsecured WiFi. This situation underscores the pressing need for robust WiFi hotspot security and adherence to cybersecurity best practices to safeguard against wallet approval scams that prey on unsuspecting users. As the digital landscape evolves, understanding and addressing public WiFi vulnerabilities become vital for the safety of assets, including the growing importance of crypto wallet safety in an interconnected world.
As the digital revolution continues to shape our everyday experiences, the dangers of using unsecured internet connections in public spaces are becoming increasingly pronounced. Public wireless networks, often seen as convenient avenues for accessing the internet, carry significant risks that can lead to severe financial losses and privacy breaches. Inadequate protection for devices connected to these networks can expose users to various cyber threats, including phishing schemes and unauthorized data access. Consequently, many individuals must remain vigilant regarding the security of their online transactions, especially when it involves cryptocurrency and related digital assets. Adopting comprehensive practices for safeguarding personal information while on the move can mitigate these risks and foster a more secure internet experience.
Understanding Public WiFi Risks for Crypto Users
Public WiFi networks are often easy targets for cybercriminals looking to exploit unsuspecting users. When you connect to an open network, such as those found in cafes, libraries, or hotels, your devices become part of a shared environment where data can be intercepted. Attackers may utilize tools like packet sniffers to capture sensitive information, including wallet credentials and personal data. In addition, methods such as ARP spoofing or DNS attacks can redirect users to fraudulent sites, leading to potential compromises of their crypto assets. These risks underline the necessity of employing robust cybersecurity practices when using any public WiFi.
Moreover, the nature of the transactions associated with cryptocurrency can further complicate matters. Unlike traditional banking, where transactions might take hours or days to clear, crypto transactions occur almost instantaneously. This speed can unwittingly encourage users to act carelessly, especially when they feel secure on what appears to be a trusted WiFi connection. Understanding the landscape of public WiFi risks is essential not only for protecting funds but also for maintaining overall cybersecurity, as the implications of a successful attack can be detrimental.
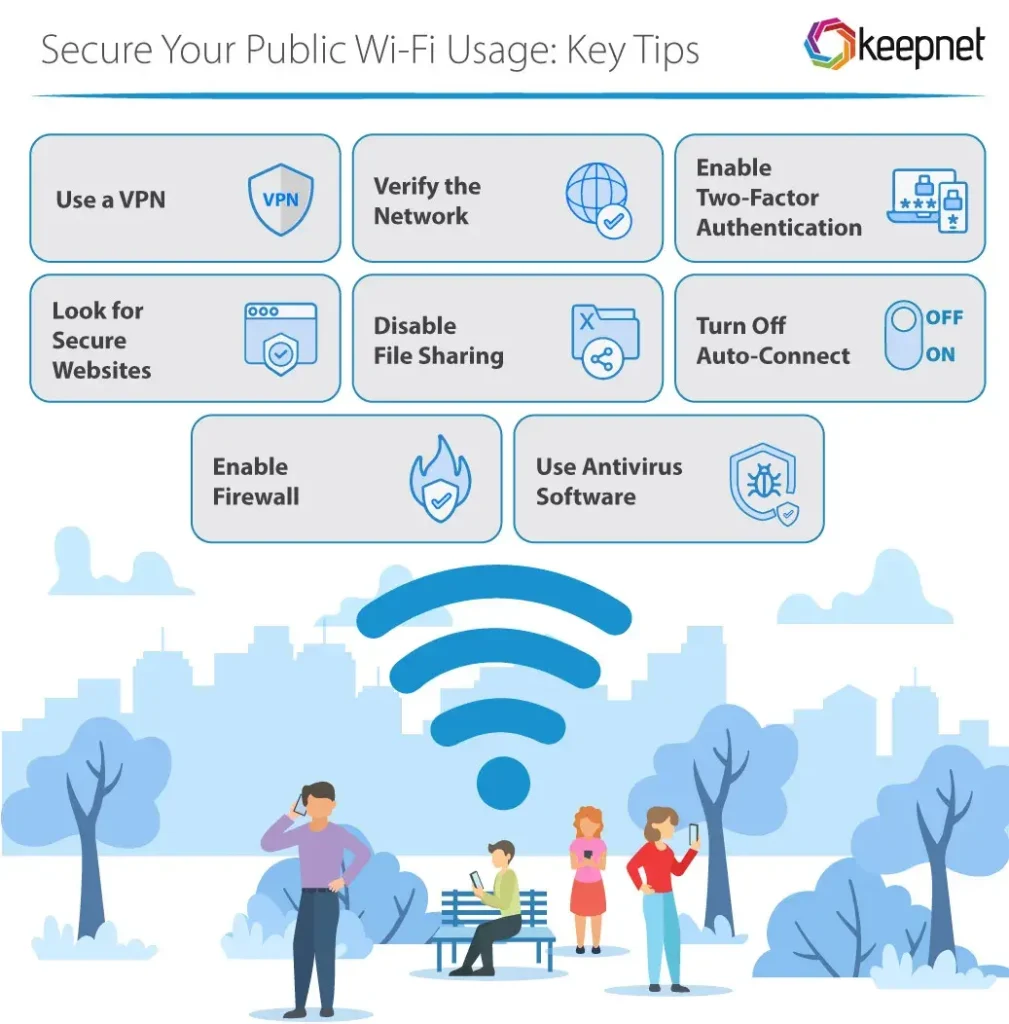
Best Practices for WiFi Hotspot Security
Practicing safe habits when connecting to WiFi hot spots can significantly reduce your risk of falling victim to cyberattacks. Utilizing a Virtual Private Network (VPN) while accessing public networks is one of the most effective strategies. A VPN encrypts your internet connection, making it much harder for cybercriminals to intercept your data. Furthermore, avoid accessing sensitive information or conducting high-risk transactions on public networks, particularly when it comes to crypto wallets, as these actions can expose you to malicious attacks.
It’s also crucial to ensure that your devices are secure before connecting to any public WiFi. Keeping your operating system, browsers, and wallet applications updated minimizes the chances of vulnerabilities being exploited by attackers. Additionally, using mobile hotspots instead of public WiFi, when possible, offers a more secure alternative for accessing the internet. By adopting these best practices for WiFi hotspot security, you bolster the protection of your crypto assets against a range of cyber threats.
The Consequences of Wallet Approval Scams
Wallet approval scams can take many forms, often exploiting users’ trust in familiar platforms and processes. As seen in the case of the crypto user who lost $5,000, seemingly harmless actions—like approving a transaction on a DeFi interface—can have dire consequences. Attackers craftily disguise malicious requests to look like standard operations, leading users to unwittingly grant permissions that allow unauthorized access to their wallets. Once such approvals are granted, the attacker can transfer assets at will, often making it difficult for victims to recover their funds.
Understanding the layering of these scams highlights the importance of vigilance in the crypto world. To avert such situations, cryptocurrency users should adopt stringent reviews of their wallet permissions regularly and remain skeptical of unsolicited transaction requests. It is crucial to learn the patterns of potential wallet approval scams and to educate others in the community about such risks. By sharing knowledge and experiences, the crypto community can effectively safeguard against these prevalent threats.
Maintaining Crypto Wallet Safety
Maintaining the safety of your crypto wallet requires a multifaceted approach that emphasizes security best practices. This includes diversifying your assets across multiple wallets, using hardware wallets for larger sums, and ensuring that your hot wallets are only used for smaller, everyday transactions. Monitoring wallet activities regularly, including scrutinizing permissions granted to applications, should become a standard practice for every crypto user. This vigilance helps deter potential abuses and reinforces a proactive attitude towards wallet safety.
In addition to managing permissions, users must exercise caution when sharing wallet-related information. Regularly reviewing the terms of service for any DeFi platform you use can help identify potential risks associated with wallet approvals. Awareness of the signs of scams—such as unsolicited offers or too-good-to-be-true investment opportunities—also plays a pivotal role in maintaining crypto wallet safety. Ultimately, combining these strategies can significantly bolster your defenses against the multitude of threats that exist in the cryptocurrency space.
Cybersecurity Best Practices for Crypto Enthusiasts
Cybersecurity should be a top priority for anyone involved in the cryptocurrency space. Employing strong, unique passwords for wallets and related accounts enhances your security posture significantly. Using two-factor authentication (2FA) adds an additional layer of protection, ensuring that even if passwords are compromised, your accounts remain secure from uninvited access. In combination with these practices, periodic reviews and updates to your security measures are essential as the threat landscape evolves constantly.
Another critical aspect of cybersecurity best practices is education. Engaging with communities focused on cryptocurrency and security can provide insights into emerging threats and effective countermeasures. Learning about recent hacks, scams, and their methodologies can equip users with the knowledge to avoid similar pitfalls. Overall, a well-informed approach, supported by robust security measures, is crucial for safeguarding your crypto wallet in an increasingly dangerous digital landscape.
Risks of Discussing Crypto Holdings in Public
Public discussions about personal investments, especially in volatile markets like cryptocurrency, can inadvertently attract unwanted attention from potential scammers. Sharing your involvement in crypto, be it through casual conversations or as a boastful display, exposes you to risks, as attackers often exploit this information to tailor their schemes. The attackers in public settings can easily overhear conversations about crypto holdings and preferences, giving them invaluable insight into how to execute their attacks.
Moreover, these casual mentions can serve as reconnaissance for attackers who may be watching and waiting for the right moment to strike. The illusion of safety in social settings may lead individuals to underestimate the potential risks involved in discussing their financial status. To combat this, it is advisable to maintain discretion by avoiding public dialogues about crypto holdings and revealing wallet details only in secure and private environments.
The Importance of Using Trusted Networks
Using trusted networks when engaging in cryptocurrency transactions is paramount for ensuring the security of your assets. Connecting to established, secure connections, such as encrypted WiFi networks or personal mobile hotspots, can significantly mitigate the risk of attacks that exploit open WiFi vulnerabilities. When traveling or accessing services outside your typical environment, evaluating the safety of the network before connecting can provide an additional layer of protection for your crypto wallet.
In practice, this means prioritizing the use of recognized private networks and avoiding public hotspots for any sensitive transactions related to cryptocurrency. Because public networks often lack sufficient security measures, they can be breeding grounds for attacks designed to steal sensitive user information. Therefore, the simple act of connecting to trusted networks not only safeguards your crypto wallet but also helps establish good cybersecurity hygiene in your daily digital interactions.
Evaluating Transactions Before Approval
Evaluating transactions before approving them is a critical habit for anyone dealing with cryptocurrencies. Every action taken within a crypto wallet often comes with the obligation to approve certain requests, which can sometimes mask malicious intents. Thoroughly reviewing the transaction details within the wallet interface—such as the recipient address and type of transaction—can help safeguard against approval abuse attacks. Being vigilant here can mean the difference between reviewing a dubious request and falling victim to financial theft.
Additionally, integrating systematic checks into your transaction approvals, like cross-referencing recipient addresses and ensuring they are known and trusted, can bolster your security. Employing a methodical approach to approvals helps users turn the blind eye into one of diligence, ensuring that all transactions are legitimate before confirming them. This level of scrutiny is vital, especially in a space where the risk of wallet approval scams is prevalent.
Developing a Personal Security Protocol for Crypto Engagement
Developing a personal security protocol for engaging with cryptocurrency can profoundly influence how effectively users protect their investments. Establishing guidelines for securely interacting with wallets, exchanges, and other platforms constitutes a defensive strategy against potential threats. Important components of this protocol might include regular software updates, comprehensive password management, and a defined process for reviewing wallet permissions regularly. This systematic approach can create a buffer against common cyber threats.
Moreover, educating oneself about the latest scams, attack vectors, and security trends forms the backbone of an effective personal security protocol. Knowledge empowers users to make informed decisions, recognize threats early, and respond swiftly to suspicious activities. By blending these practices into daily routines, cryptocurrency users can significantly enhance their protective measures and maintain a higher level of security.
Frequently Asked Questions
What are the public WiFi risks for crypto users?
Public WiFi networks are inherently insecure, exposing users to risks such as ARP spoofing and DNS manipulation. Cybercriminals can exploit these vulnerabilities to inject malicious scripts, potentially compromising crypto wallets. Avoid using public WiFi for financial transactions to mitigate these risks.
How can I enhance my crypto wallet safety on public WiFi?
To enhance crypto wallet safety, avoid connecting to public WiFi; use a secure mobile hotspot or a reputable VPN. Ensure that your devices are up-to-date and only use trusted platforms for transactions. Regularly review wallet permissions and limit exposure of your crypto holdings in public.
What is WiFi hotspot security and why is it important for cryptocurrency transactions?
WiFi hotspot security involves configuring a secure connection to ensure data privacy. It is crucial for cryptocurrency transactions as public and unsecured networks can lead to unauthorized access to wallets and funds. Always prioritize secure hotspots when managing crypto assets.
What are common wallet approval scams associated with public WiFi?
Wallet approval scams often occur when users unknowingly sign malicious transaction requests while connected to untrusted public WiFi. Attackers may inject code that alters new approval requests, allowing them unrestricted access to funds. Vigilance and caution are necessary while approving any requests.
What are the best cybersecurity practices for using public WiFi while handling cryptocurrencies?
Best cybersecurity practices include avoiding public WiFi for financial transactions, using a VPN, ensuring strong device security with updates, and never discussing crypto holdings in public. Always treat every device connection as a potential threat and confirm URL legitimacy before entering sensitive information.
| Key Point | Details |
|---|---|
| Public WiFi Risks | Open WiFi networks can expose users to various attacks such as ARP spoofing and DNS manipulation. |
| Social Engineering | Discussing crypto in public can alert attackers to potential targets and information about wallet types. |
| Approval Abuse | Signing a seemingly normal transaction can allow attackers to gain standing permissions to drain funds later. |
| Precautionary Measures | Avoid public WiFi for wallet interactions; use mobile hotspots or reputable VPNs. |
| Regular Security Practices | Review and revoke on-chain approvals, spread funds across wallets, and maintain strong operational security. |
Summary
Public WiFi security is a critical concern for all internet users, especially those involved in cryptocurrency. The incident involving the loss of $5,000 from a hot wallet due to vulnerabilities associated with open WiFi networks underlines the importance of being vigilant when utilizing public internet connections. Attackers can leverage both technical exploits and social cues to target unsuspecting users. To protect yourself while accessing public networks, it is essential to employ precautions like using a mobile hotspot, conducting only secure transactions, and ensuring your device’s security settings are up to date.
Related: More from Regulation & Policy | EU Crypto Taxes: Practical Implications Explained | UK FCA to Consider Cryptos for Gambling Payments